Core isolation is a security feature of Microsoft Windows that protects important core processes of Windows from malicious software by isolating them in memory. It does this by running those core processes in a virtualized environment.
Note: What you see on the Core isolation page may vary a bit depending on what version of Windows you're running.
Memory integrity
Memory integrity, also known as Hypervisor-protected Code Integrity (HVCI) is a Windows security feature that makes it difficult for malicious programs to use low-level drivers to hijack your computer.
A driver is a piece of software that lets the operating system (Windows in this case) and a device (like a keyboard or a webcam, for two examples) talk to each other. When the device wants Windows to do something it uses the driver to send that request.
Tip: Want to know more about drivers? See What is a driver?
Memory integrity works by creating an isolated environment using hardware virtualization.
Think of it like a security guard inside a locked booth. This isolated environment (the locked booth in our analogy) prevents the memory integrity feature from being tampered with by an attacker. A program that wants to run a piece of code which may be dangerous has to pass the code to memory integrity inside that virtual booth so that it can be verified. When memory integrity is comfortable that the code is safe it hands the code back to Windows to run. Typically, this happens very quickly.
Without memory integrity running, the "security guard" stands right out in the open where it's much easier for an attacker to interfere with or sabotage the guard, making it easier for malicious code to sneak past and cause problems.
How do I manage memory integrity?
In most cases memory integrity is on by default in Windows 11, and can be turned on for Windows 10.
To turn it on or off:
-
Select the Start button and type “Core isolation”.
-
Select the Core Isolation system settings from the search results to open the Windows security app.
On the Core isolation page, you’ll find Memory integrity along with the toggle to turn it on or off.
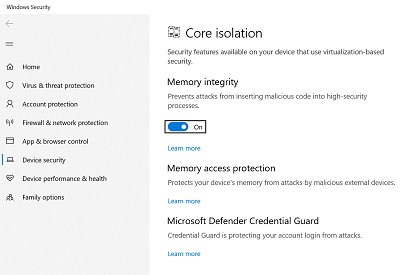
Important: For safety we recommend having memory integrity turned on.
To use memory integrity, you must have hardware virtualization enabled in your system’s UEFI or BIOS.
What if it says I have an incompatible driver?
If memory integrity fails to turn on it may tell you that you have an incompatible device driver already installed. Check with the manufacturer of the device to see if they have an updated driver available. If they don’t have compatible driver available, you might be able to remove the device or app that uses that incompatible driver.

Note: If you try to install a device with an incompatible driver after turning on memory integrity, you may see the same message. If so, the same advice applies - check with the device manufacturer to see if they have an updated driver you can download, or don’t install that particular device until a compatible driver is available.
Kernel-mode Hardware-enforced Stack Protection
Kernel-mode Hardware-enforced Stack Protection is a hardware-based Windows security feature that makes it difficult for malicious programs to use low-level drivers to hijack your computer.
A driver is a piece of software that lets the operating system (Windows in this case) and a device like a keyboard or a webcam for example, talk to each other. When the device wants Windows to do something it uses the driver to send that request.
Tip: Want to know more about drivers? See What is a driver?
The Kernel-mode Hardware-enforced Stack Protection works by preventing attacks that modify return addresses in kernel-mode memory to launch malicious code. This security feature requires a CPU that contains the ability to verify the return addresses of running code.
When executing code in kernel-mode, return addresses on the kernel-mode stack can be corrupted by malicious programs or drivers in order to redirect normal code execution to malicious code. On supported CPUs, the CPU maintains a second copy of valid return addresses on a read-only shadow stack that drivers cannot modify. If a return address on the regular stack has been modified, the CPU can detect this discrepancy by checking the copy of the return address on the shadow stack. When this discrepancy occurs, the computer prompts a stop error, sometimes known as a blue screen, to prevent the malicious code from executing.
Not all drivers are compatible with this security feature, as a small number of legitimate drivers engage in return address modification for non-malicious purposes. Microsoft has been engaging with numerous driver publishers to ensure that their latest drivers are compatible with Kernel-mode Hardware-enforced Stack Protection.
How do I manage Kernel-mode Hardware-enforced Stack Protection?
Kernel-mode Hardware-enforced Stack Protection is turned off by default.
To turn it on or off:
-
Select the Start button and type “Core isolation”.
-
Select the Core Isolation system settings from the search results to open the Windows security app.
On the Core isolation page, you’ll find Kernel-mode Hardware-enforced Stack Protection along with the toggle to turn it on or off.
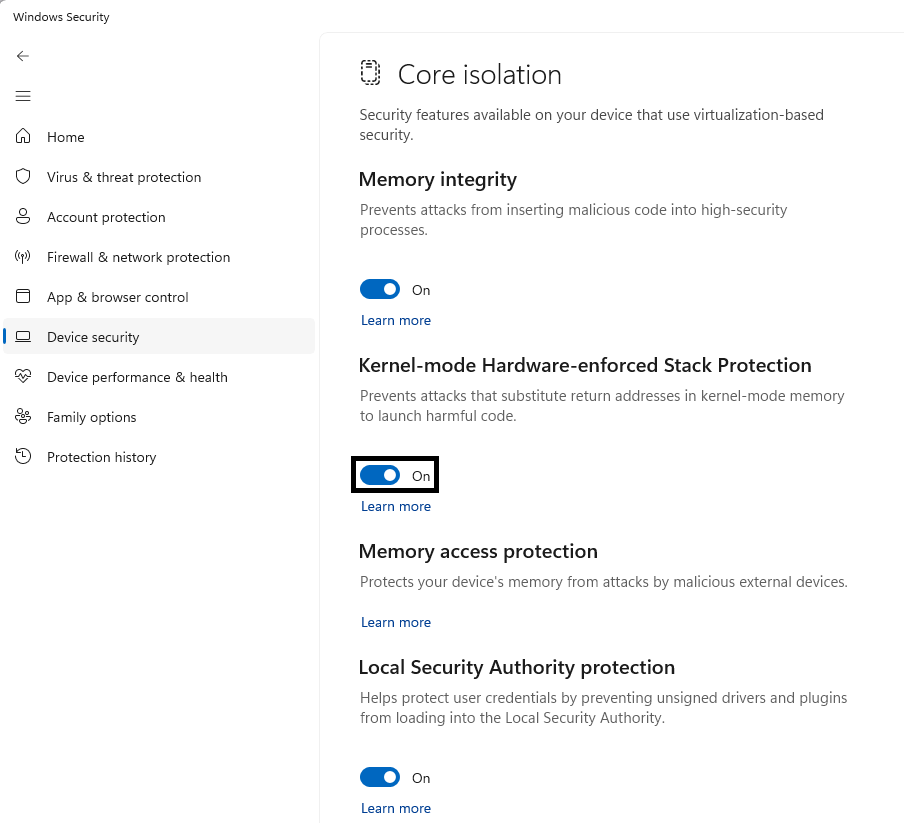
To use Kernel-mode Hardware-enforced Stack Protection, you must have Memory Integrity enabled, and you must be running a CPU that supports Intel Control-Flow Enforcement Technology or AMD Shadow Stack.
What if it says I have an incompatible driver or service?
If Kernel-mode Hardware-enforced Stack Protection fails to turn on it may tell you that you have an incompatible device driver or service already installed. Check with the manufacturer of the device or the application publisher to see if they have an updated driver available. If they don’t have a compatible driver available, you might be able to remove the device or app that uses that incompatible driver.
Some applications may install a service instead of a driver during the application's installation and install the driver only when the application is launched. For more accurate detection of incompatible drivers, services that are known to be associated with incompatible drivers are also enumerated.
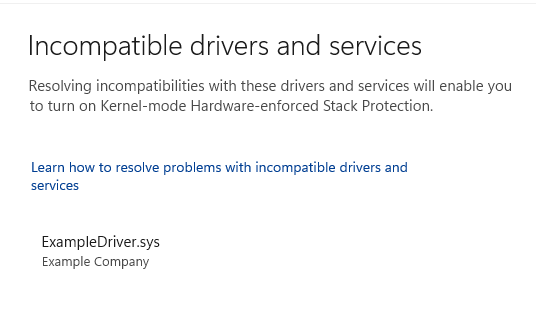
Note: If you try to install a device or app with an incompatible driver after turning on Kernel-mode Hardware-enforced Stack Protection, you may see the same message. If so, the same advice applies - check with the device manufacturer or app publisher to see if they have an updated driver you can download, or don’t install that particular device or app until a compatible driver is available.
Memory access protection
Also known as "Kernel DMA protection" this protects your device against attacks that can occur when a malicious device is plugged into a PCI (Peripheral Component Interconnect) port like a Thunderbolt port.
A simple example of one of these attacks would be if someone leaves their PC for a quick coffee break, and while they were away, an attacker steps in, plugs in a USB-like device and walks away with sensitive data from the machine, or injects malware that allows them to control the PC remotely.
Memory access protection prevents these kinds of attacks by denying direct access to the memory to those devices except under special circumstances, particularly when the PC is locked or the user is signed out.
We recommend having memory access protection turned on.
Tip: If you'd like more technical detail about this see Kernel DMA Protection.
Firmware protection
Every device has some software that's been written to the read-only memory of the device - basically written to a chip on the system board - that is used for the basic functions of the device, such as loading the operating system that runs all the apps we're used to using. Since that software is difficult (but not impossible) to modify we refer to it as firmware.
Because the firmware loads first and runs under the operating system, security tools and features that run in the operating system have a difficult time detecting it or defending against it. Like a house that depends on a good foundation to be secure, a computer needs its firmware to be secure in order to ensure that the operating system, applications, and customer data on that computer are safe.
Windows Defender System Guard is a set of features that helps to ensure that attackers can't get your device to start with untrusted or malicious firmware.
We recommend that you have it turned on if your device supports it.
Platforms that offer firmware protection typically also protect the System Management Mode (SMM), a highly privileged operating mode, to varying degrees. You can expect one of the three values, with a higher number indicating a greater degree of SMM protection:
-
Your device meets firmware protection version one: this offers the foundational security mitigations to help SMM resist exploitation by malware, and prevents exfiltration of secrets from the OS (including VBS)
-
Your device meets firmware protection version two: in addition to firmware protection version one, version two ensures that SMM can't disable Virtualization-based Security (VBS) and kernel DMA protections
-
Your device meets firmware protection version three: in addition to firmware protection version two, it further hardens the SMM by preventing access to certain registers that have the ability to compromise the OS (including VBS)
Tip: If you'd like more technical detail about this, see Windows Defender System Guard: How a hardware-based root of trust helps protect Windows
Local Security Authority protection
Local Security Authority (LSA) protection is a Windows security feature to help prevent the theft of credentials used for signing into Windows.
The Local Security Authority (LSA) is a crucial process in Windows involved in user authentication. It’s responsible for verifying credentials during the login process and managing authentication tokens and tickets used to enable single sign-on for services. LSA protection helps prevent untrusted software from running inside LSA or from accessing LSA memory.
How do I manage Local Security Authority protection
LSA protection is turned on by default on new installs of Windows 11 version 22H2 and 23H2 on enterprise managed devices. It’s turned on by default on all new installs of Windows 11 version 24H2 and later.
If you are upgrading to Windows 11 24H2 and LSA protection isn’t already enabled, LSA protection will attempt to enable after the upgrade. LSA protection will enter an evaluation mode following the upgrade and will check for compatibility issues during a 5-day period. If there are no issues detected, then LSA protection will be turned on automatically on your next reboot after the evaluation window has ended.
To turn it on or off:
-
Select Start on the taskbar and type “Core isolation”.
-
Select the Core Isolation system settings from the search results to open the Windows security app.
On the Core isolation page, you’ll find Local Security Authority protection along with the toggle to turn it on or off. After you have changed the setting, you must reboot for it to take effect.
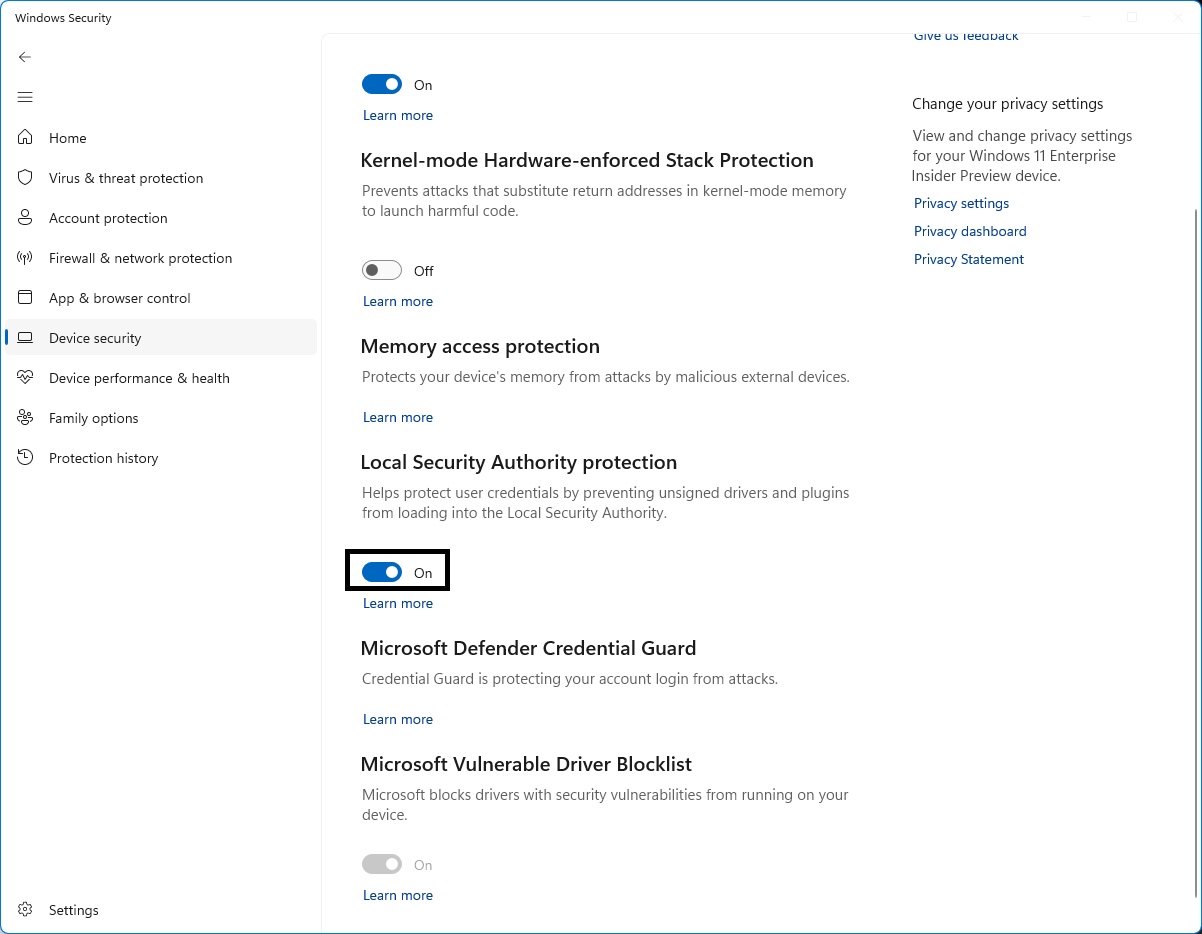
What if I have incompatible software?
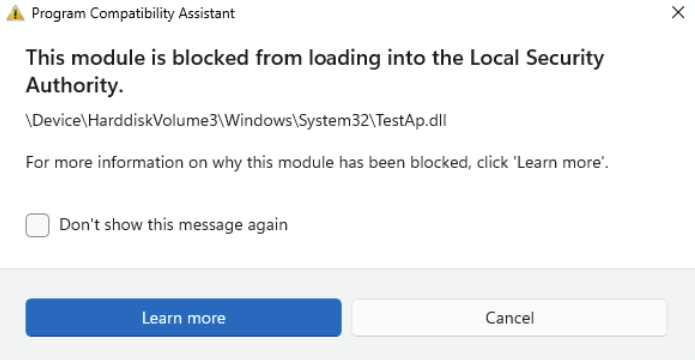
If LSA protection is enabled and it blocks the loading of software into the LSA service, a notification will be shown indicating the file that was blocked. You might be able to remove the software loading the file or you can disable future warnings for that file when it’s blocked from loading into LSA.
Microsoft Defender Credential Guard
Note: Microsoft Defender Credential Guard only appears on devices running Enterprise versions of Windows 10 or 11.
While you're using your work or school computer it will be quietly signing into and gaining access to a variety of things such as files, printers, apps, and other resources in your organization. Making that process secure, yet easy for the user, means that your computer has a number of authentication tokens (often referred to as "secrets") on it at any given time.
If an attacker can gain access to one, or more, of those secrets they might be able to use them to gain access to the organizational resource (sensitive files, etc) that the secret is for. Microsoft Defender Credential Guard helps to protect those secrets by putting them in a protected, virtualized, environment where only certain services can access them when necessary.
We recommend that you have it turned on if your device supports it.
Tip: If you'd like more technical detail about this, see How Defender Credential Guard works.
Microsoft Vulnerable Driver Blocklist
A driver is a piece of software that lets the operating system (Windows in this case) and a device (like a keyboard or a webcam, for two examples) talk to each other. When the device wants Windows to do something it uses the driver to send that request. Because of this, drivers have a lot of sensitive access in your system.
Starting with the Windows 11 2022 update we now have a blocklist of drivers that have known security vulnerabilities, have been signed with certificates that have been used to sign malware, or that circumvent the Windows Security Model.
If you have memory integrity, Smart App Control, or Windows S mode on, the vulnerable driver blocklist will be on too.










