Summary
Transport Layer Security (TLS) 1.0 and 1.1 are security protocols for creating encryption channels over computer networks. Microsoft has supported them since Windows XP and Windows Server 2003. However, regulatory requirements are changing. Also, there are new security weaknesses in TLS 1.0. So, Microsoft recommends that you remove TLS 1.0 and 1.1 dependencies. We also recommend that you disable TLS 1.0 and 1.1 at the operating system level where possible. For more details, see TLS 1.0 and 1.1 disablement. In the September 20, 2022 preview update, we will disable TLS 1.0 and 1.1 by default for applications based on winhttp and wininet. This is part of an ongoing effort. This article will help you to re-enable them. These changes will be reflected after installing Windows updates released on or after September 20, 2022.
Behavior when accessing TLS 1.0 and 1.1 links in the browser
After September 20, 2022, a message will appear when your browser opens a website that uses TLS 1.0 or 1.1. See Figure 1. The message states that the site uses an outdated or unsafe TLS protocol. To address this, you can update the TLS protocol to TLS 1.2 or above. If this is not possible, you can enable TLS as discussed in Enabling TLS version 1.1 and below.
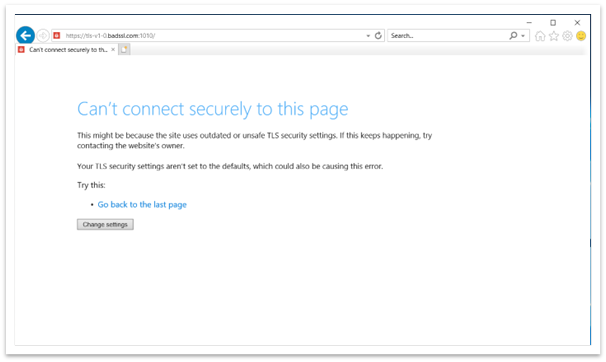
Figure 1: Browser window when accessing TLS 1.0 and 1.1 webpage
Behavior when accessing TLS 1.0 and 1.1 links in winhttp applications
After the update, applications based on winhttp might fail. The error message is, "ERROR_WINHTTP_SECURE_FAILURE while performing WinHttpSendRequest operation."
Behavior when accessing TLS 1.0 and 1.1 links in custom UI applications based on winhttp or wininet
When an application tries to create a connection using TLS 1.1 and below, the connection might appear to fail. When you close an application or it stops working, the Program Compatibility Assistant (PCA) dialog appears as shown in Figure 2.
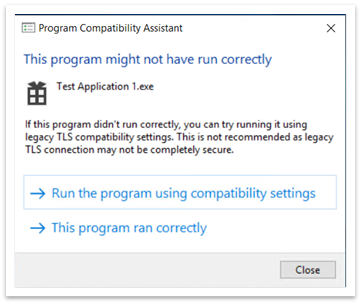
Figure 2: Program Compatibility Assistant dialog after closing an application
The PCA dialog states, “This program might not have run correctly.” Under that, there are two options:
-
Run the program using compatibility settings
-
This program ran correctly
Run the program using compatibility settings
When you choose this option, the application reopens. Now, all the links that use TLS 1.0 and 1.1 work correctly. From then on, no PCA dialog will appear. The Registry Editor adds entries to the following paths:
-
Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store.
-
Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers.
If you chose this option by mistake, you can delete these entries. If you delete them, you will see the PCA dialog the next time you open the app.
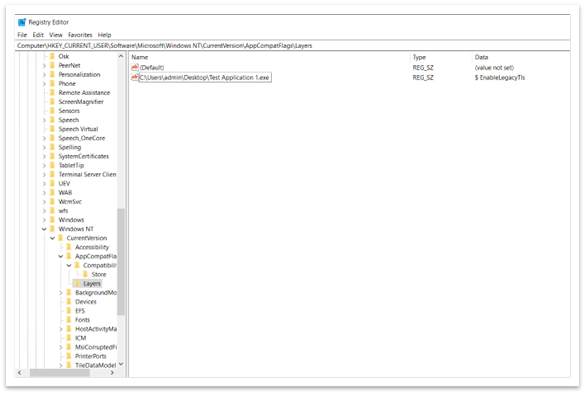
Figure 3: List of programs that should run using compatibility settings
This program ran correctly
When you choose this option, the application closes normally. The next time you reopen the application, no PCA dialog appears. The system blocks all TLS 1.0 and 1.1 content. The Registry Editor adds the following entry to the path Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store. See Figure 4. If you chose this option by mistake, you can delete this entry. If you delete the entry, you will see the PCA dialog the next time you open the app.
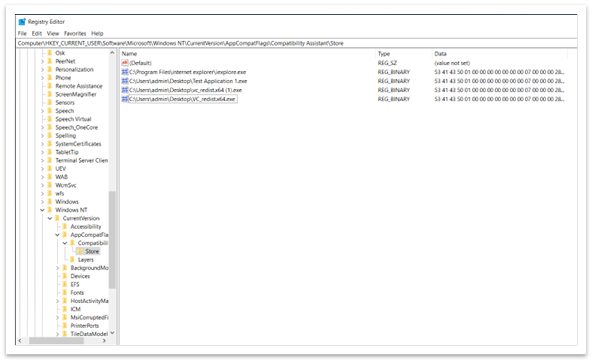
Figure 4: Entry in Registry Editor stating that the app ran correctly
Important Legacy TLS protocols are only enabled for specific applications. This is true even though they are disabled in system-wide settings.
Enable TLS version 1.1 and below (wininet and Internet Explorer settings)
We do not recommend enabling TLS 1.1 and below because they are no longer considered secure. They are vulnerable to various attacks, such as the POODLE attack. So, before enabling TLS 1.1, do one of the following:
-
Check if a newer version of the application is available.
-
Ask the app developer to make configuration changes in the app to remove dependency on TLS 1.1 and below.
In case none of the solutions work, then there are two ways to enable legacy TLS protocols in system-wide settings:
-
Internet Options
-
Group Policy Editor
Internet Options
To open Internet Options, type Internet Options in the search box on the taskbar. You can also select Change settings from the dialog shown in Figure 1. On the Advanced tab, scroll down in the Settings panel. There you can enable or disable TLS protocols.
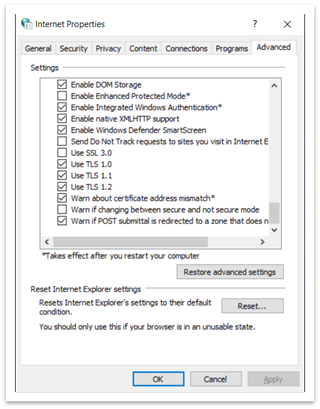
Figure 5: Internet Properties dialog
The Group Policy Editor
To open the Group Policy Editor, type gpedit.msc in the taskbar search box. A window like the one shown in Figure 6 appears.
Figure 6: Group Policy Editor window
-
Navigate to Local Computer Policy > (Computer Configuration or User Configuration) > Administrative Templets > Windows Components > Internet Explorer > Internet Control Panel > Advanced Page > Turn off encryption support. See Figure 7.
-
Double click Turn off encryption support.
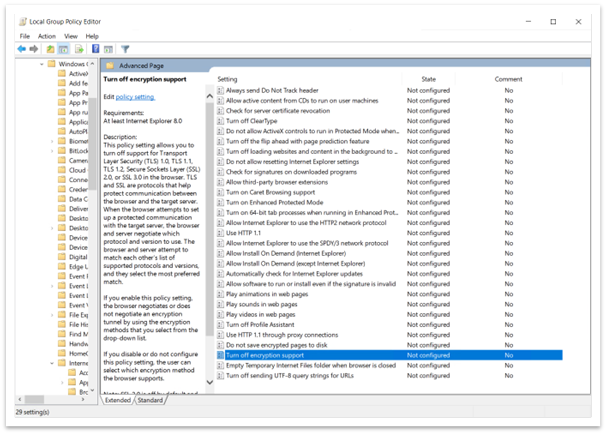
Figure 7: Path to turn off encryption support in Group Policy Editor
-
Select the Enabled option. Then use the dropdown list to select the TLS version you want to enable as shown in Figure 8.
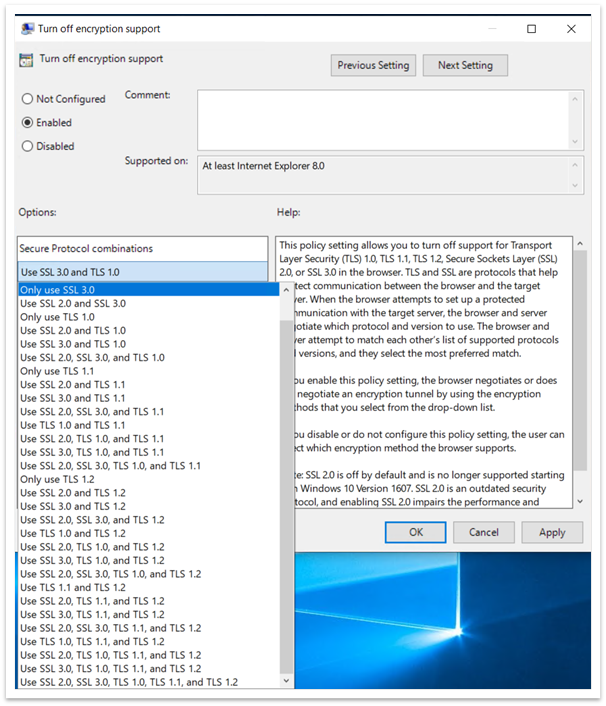
Figure 8: Enable Turn off encryption support and dropdown list
Once you enable the policy in the Group Policy Editor, you cannot change it in Internet Options. For example, if you select Use SSL3.0 and TLS 1.0, all other options will be unavailable in Internet Options. See Figure 9. You cannot change any of the settings in Internet Options if you enable Turn off encryption support in the Group Policy Editor.
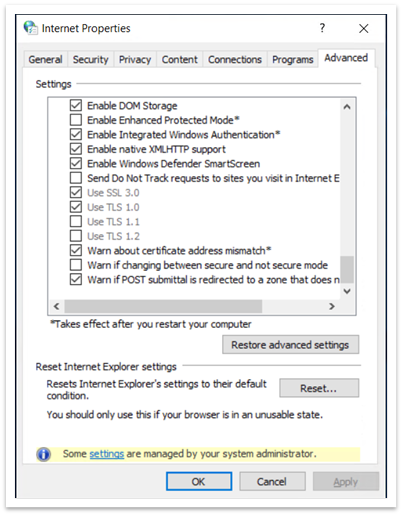
Figure 9: Internet Options showing unavailable SSL and TLS settings
Enable TLS version 1.1 and below (winhttp settings)
See Update to enable TLS 1.1 and TLS 1.2 as default secure protocols in WinHTTP in Windows.
Important registry paths (wininet and Internet Explorer settings)
-
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings
-
Here you can find SecureProtocols, which stores the value of the currently enabled protocols if you use the Group Policy Editor.
-
-
Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
-
Here you can find SecureProtocols, which stores the value of currently enabled protocols if you use Internet Options.
-
-
Group Policy SecureProtocols will take precedence over the one set by Internet Options.
Enabling insecure TLS fallback
The modifications above will enable TLS 1.0 and TLS 1.1. However, they won’t enable TLS fallback. To enable TLS fallback, you must set EnableInsecureTlsFallback to 1 in the registry under the paths below.
-
To change settings: SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\winhttp
-
To set policy: SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings
If EnableInsecureTlsFallback is not present, then you must create a new DWORD entry and set it to 1.
Important registry paths
-
ForceDefaultSecureProtocols
-
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\winhttp
-
It is FALSE by default. Setting a non zero value will stop applications from setting custom protocols using the winhttp option.
-
-
EnableInsecureTlsFallback
-
To change settings: SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\winhttp
-
To set policy: SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings
-
It is FALSE by default. Setting a non zero value will enable applications to fall back to unsecure protocols (TLS1.0 and 1.1) if the handshake fails with secure protocols (tls1.2 and above).
-










