IMPORTANT You should apply the Windows security update released on or after July 9, 2024, as part of your regular monthly update process.
This article applies to those organizations who should begin evaluating mitigations for a publicly disclosed Secure Boot bypass leveraged by the BlackLotus UEFI bootkit. Additionally, you might want to take a proactive security stance or to start to prepare for the rollout. Note that this malware requires physical or administrative access to the device.
CAUTION After the mitigation for this issue is enabled on a device, meaning the mitigations have been applied, it cannot be reverted if you continue to use Secure Boot on that device. Even reformatting of the disk will not remove the revocations if they have already been applied. Please be aware of all the possible implications and test thoroughly before you apply the revocations that are outlined in this article to your device.
In this article
Summary
This article describes the protection against the publicly disclosed Secure Boot security feature bypass that uses the BlackLotus UEFI bootkit tracked by CVE-2023-24932, how to enable the mitigations, and guidance on bootable media. A bootkit is a malicious program that is designed to load as early as possible in a devices boot sequence to control the operating system start.
Secure Boot is recommended by Microsoft to make a safe and trusted path from the Unified Extensible Firmware Interface (UEFI) through the Windows kernel Trusted Boot sequence. Secure Boot helps prevent bootkit malware in the boot sequence. Disabling Secure Boot puts a device at risk of being infected by bootkit malware. Fixing the Secure Boot bypass described in CVE-2023-24932 requires revoking boot managers. This could cause issues for some device boot configurations.
Mitigations against the Secure Boot bypass detailed in CVE-2023-24932 are included in the Windows security updates that were released on or after July 9, 2024. However, these mitigations are not enabled by default. With these updates, we recommend that you begin evaluating these changes within your environment. The complete schedule is described in the Timing of updates section.
Before you enable these mitigations, you should thoroughly review the details in this article and determine whether you have to enable the mitigations or wait for a future update from Microsoft. If you choose to enable the mitigations, you must verify your devices are updated and ready, and understand the risks described in this article.
Take Action
|
For this release, the following steps should be followed: Step 1: Install the Windows security update released on or after July 9, 2024, on all supported versions. Step 2: Evaluate the changes and how they affect your environment. Step 3: Enforce the changes. |
Scope of Impact
All Windows devices with Secure Boot protections enabled are affected by the BlackLotus bootkit. Mitigations are available for supported versions of Windows. For the full list, please see CVE-2023-24932.
Understanding the risks
Malware Risk: For the BlackLotus UEFI bootkit exploit described in this article to be possible, an attacker must gain administrative privileges on a device or gain physical access to the device. This can be done by accessing the device physically or remotely, such as by using a hypervisor to access VMs/cloud. An attacker will commonly use this vulnerability to continue controlling a device that they can already access and possibly manipulate. Mitigations in this article are preventive and not corrective. If your device is already compromised, contact your security provider for help.
Recovery Media: If you encounter an issue with the device after applying the mitigations and the device becomes unbootable, you might be unable to start or recover your device from existing media. Recovery or install media will need to be updated so that it will work with a device that has the mitigations applied.
Firmware Issues: When Windows applies the mitigations described in this article, it must rely on the UEFI firmware of the device to update the Secure Boot values (the updates are applied to the Database Key (DB) and the Forbidden Signature Key (DBX)). In some cases, we have experience with devices that fail the updates. We are working with device manufacturers to test these key updates in as many devices as possible.
NOTE Please first test these mitigations on a single device per device class in your environment to detect possible firmware issues. Do not deploy broadly before confirming all the device classes in your environment have been evaluated.
BitLocker Recovery: Some devices may go into BitLocker recovery. Be sure to retain a copy of your BitLocker recovery key before enabling the mitigations.
Known Issues
Firmware Issues: Not all device firmware will successfully update the Secure Boot DB or DBX. In the cases that we are aware of, we have reported the issue to the device manufacturer. See KB5016061: Secure Boot DB and DBX variable update events for details on logged events. Please contact the device manufacturer for firmware updates. If the device is not in support, Microsoft recommends upgrading the device.
Known firmware issues:
NOTE The following known issues have no impact on, and will not prevent the installation of the July 9, 2024 updates. In most cases, the mitigations will not apply where known issues exist. See details called out in each known issue.
-
HP: HP identified an issue with mitigation installation on HP Z4G4 Workstation PCs and will release an updated Z4G4 UEFI firmware (BIOS) in the coming weeks. To ensure successful installation of the mitigation, it will be blocked on Desktop Workstations until the update is available. Customers should always update to the latest system BIOS before applying the mitigation.
-
HP devices with Sure Start Security: These devices need the latest firmware updates from HP to install the mitigations. The mitigations are blocked until the firmware is updated. Install the latest firmware update from HPs support page — Official HP Drivers and Software Download | HP Support.
-
Arm64-based devices: The mitigations are blocked due to known UEFI firmware issues with Qualcomm-based devices. Microsoft is working with Qualcomm to address this issue. Qualcomm will provide the fix to device manufacturers. Contact your device manufacturer to determine if a fix for this issue is available. Microsoft will add detection to allow the mitigations to be applied on devices when the fixed firmware is detected. If your Arm64-based device does not have Qualcomm firmware, configure the following registry key to enable the mitigations.
Registry Subkey
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecureBoot
Key Value name
SkipDeviceCheck
Data Type
REG_DWORD
Data
1
-
Apple: Mac computers that have the Apple T2 Security Chip support Secure Boot. However, updating UEFI security related variables is available only as part of macOS updates. Boot Camp users are expected to see an event log entry of Event ID 1795 in Windows related to these variables. For more information about this log entry, see KB5016061: Secure Boot DB and DBX variable update events.
-
VMware: On VMware-based virtualization environments, a VM using an x86-based processor with Secure Boot enabled, will fail to boot after applying the mitigations. Microsoft is coordinating with VMware to address this issue.
-
TPM 2.0-based systems: These systems that run Windows Server 2012 and Windows Server 2012 R2 cannot deploy the mitigations released in the July 9, 2024 security update because of known compatibility issues with TPM measurements. The July 9, 2024 security updates will block mitigations #2 (boot manager) and #3 (DBX update) on affected systems. Microsoft is aware of the issue and an update will be released in the future to unblock TPM 2.0-based systems. To check your TPM version, right-click Start, click Run, and then type tpm.msc. On the bottom-right of the center pane under TPM Manufacturer Information, you should see a value for Specification Version.
-
Symantec Endpoint Encryption: Secure Boot mitigations cannot be applied to systems who have installed Symantec Endpoint Encryption. Microsoft and Symantec are aware of the issue and will be addressed in future update.
Guidelines for this release
For this release, follow these two steps.
Step 1: Install the Windows security update Install the Windows monthly security update released on or after July 9, 2024, on supported Windows devices. These updates include mitigations for CVE-2023-24932 but are not enabled by default. All Windows devices should complete this step whether or not you plan to deploy the mitigations.
Step 2: Evaluate the changes We encourage you to do the following:
-
Understand the first two mitigations that allow updating the Secure Boot DB and updating the boot manager.
-
Review the updated schedule.
-
Begin testing the first two mitigations against representative devices from your environment.
-
Begin planning for the deployment.
Step 3: Enforce the changes
We encourage you to understand the risks called out in the Understanding the Risks section.
-
Understand the impact to recovery and other bootable media.
-
Begin testing the third mitigation that untrusts the signing certificate used for all previous Windows boot managers.
Mitigation deployment guidelines
Before following these steps for applying the mitigations, install the Windows monthly servicing update released on or after July 9, 2024, on supported Windows devices. This update includes mitigations for CVE-2023-24932 but they are not enabled by default. All Windows devices should complete this step regardless of your plan to enable the mitigations.
NOTE If you use BitLocker, make sure that your BitLocker recovery key has been backed-up. You can run the following command from an Administrator command prompt and note the 48-digit numerical password:
manage-bde -protectors -get %systemdrive%
To deploy the update and apply the revocations, follow these steps:
-
Install the updated certificate definitions to the DB.
This step will add the “Windows UEFI CA 2023” certificate to the UEFI “Secure Boot Signature Database” (DB). By adding this certificate to the DB, the device firmware will trust boot applications signed by this certificate.
-
Open an Administrator command prompt and set the regkey to perform the update to DB by entering the following command:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x40 /f
IMPORTANT Make sure to restart the device two times to complete the installation of the update before proceeding to Steps 2 and 3.
-
Run the following PowerShell command as an Administrator and verify that the DB has been successfully updated. This command should return True.
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match 'Windows UEFI CA 2023'
-
-
Update the Boot Manager on your device.
This step will install a boot manager application on your device which is signed with the “'Windows UEFI CA 2023” certificate.
-
Open an Administrator command prompt and set the regkey to install the “'Windows UEFI CA 2023” signed boot manager:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x100 /f
-
Restart the device two times.
-
As Administrator, mount the EFI partition to get it ready for inspection:
mountvol s: /s
-
Validate that "s:\efi\microsoft\boot\bootmgfw.efi" file is signed by the “Windows UEFI CA 2023” certificate. To do this, follow these steps:
-
Click Start, type command prompt in the Search box, and then click Command Prompt.
-
In the Command Prompt window, type the following command and then press Enter:
copy S:\EFI\Microsoft\Boot\bootmgfw.efi c:\bootmgfw_2023.efi
-
In File Manager, right-click the file C:\bootmgfw_2023.efi, click Properties, and then select the Digital Signatures tab.
-
In the Signature list, confirm that the certificate chain includes Windows UEFI CA 2023. The certificate chain should match the following screenshot:
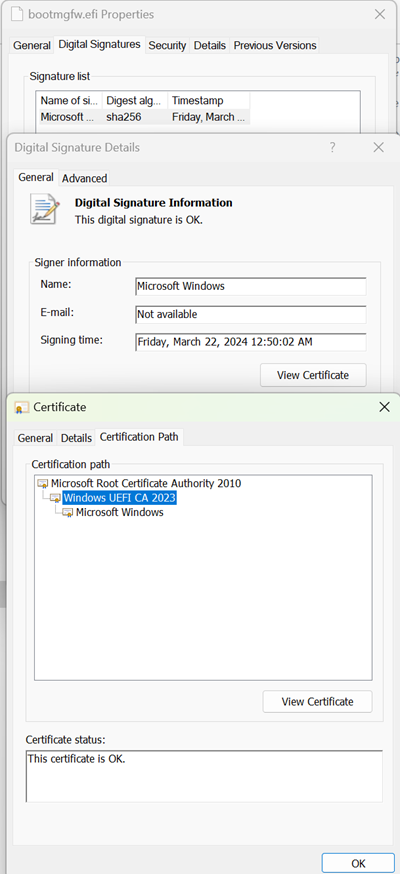
-
-
-
Enable the revocation.
The UEFI Forbidden List (DBX) is used to block untrusted UEFI modules from loading. In this step, updating the DBX will add the “Windows Production CA 2011” certificate to the DBX. This will cause all boot managers signed by this certificate to no longer be trusted.
WARNING: Before applying the third mitigation, create a recovery flash drive that can be used to boot the system. For information about how to do this, see the Updating Windows install media section.
If your system gets into a non-bootable state, follow the steps in the Recovery procedure section to reset the device to a pre-revocation state.
-
Add the “Windows Production PCA 2011” certificate to the Secure Boot UEFI Forbidden List (DBX). To do this, open a Command Prompt windows as an Administrator, type the following command, and then press Enter:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x80 /f
-
Restart the device two times and confirm that it has fully restarted.
-
Verify installation and revocation list was successfully applied by looking for event 1037 in the event log. For information about Event 1037, see KB5016061: Secure Boot DB and DBX variable update events. Or, run the following PowerShell command as Administrator and make sure it returns True:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI dbx).bytes) -match 'Microsoft Windows Production PCA 2011'
-
-
Apply the SVN update to the firmware. The Boot Manager deployed in Step 2 has a new self-revocation feature built-in. When the Boot Manager starts to run, it performs a self-check by comparing the Secure Version Number (SVN) that is stored in the firmware, with the SVN built into the Boot Manager. If the Boot Manager SVN is lower than the SVN stored in the firmware, the Boot Manager will refuse to run. This feature prevents an attacker from rolling back the Boot Manager to an older, non-updated version. In future updates, when a significant security issue is fixed in the Boot Manager, the SVN number will be incremented in both the Boot Manager and the update to the firmware. Both updates will be released in the same cumulative update to make sure that patched devices are protected. Each time the SVN is updated, any bootable media will need to be updated. Starting with the July 9, 2024, updates, the SVN is being incremented in the Boot Manager and the update to the firmware. The firmware update is optional and can be applied by following these steps:
-
Open an Administrator command prompt and run the following command to install the “'Windows UEFI CA 2023” signed boot manager:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x200 /f
-
Restart the device two times.
-
Bootable media
It will be important to update bootable media once the Deployment Phase begins in your environment.
Guidance for updating bootable media is coming with future updates to this article. See the next section to create a USB thumb drive for recovering a device.
Updating Windows install media
NOTE When creating a bootable USB thumb drive, be sure to format the drive by using the FAT32 filesystem.
You can use the Create Recovery Drive application by following these steps. This media can be used to reinstall a device in case there is a major issue such as a hardware failure, you will be able to use the recovery drive to reinstall Windows.
-
Go to a device where the July 9, 2024 updates and the first mitigation step (updating the Secure Boot DB) have been applied.
-
From the Start menu, search for “Create a Recovery Drive” control panel applet and follow the instructions to create a recovery drive.
-
With the newly created flash drive mounted (for example, as drive “D:”), run the following commands as an administrator. Type each of the following commands, and then press Enter:
COPY D:\EFI\MICROSOFT\BOOT\BCD D:\EFI\MICROSOFT\BOOT\BCD.BAK
bcdboot c:\windows /f UEFI /s D: /bootex
COPY D:\EFI\MICROSOFT\BOOT\BCD.BAK D:\EFI\MICROSOFT\BOOT\BCD
If you manage installable media in your environment by using the Update Windows installation media with Dynamic Update guidance, follow these steps. These additional steps will create a bootable flash drive that uses boot files signed by the “Windows UEFI CA 2023” signing certificate.
-
Go to a device where the July 9, 2024, updates and the first mitigation step (updating the Secure Boot DB) has been applied.
-
Follow the steps in the link below to create media with the July 9, 2024, updates. Update Windows installation media with Dynamic Update
-
Place the contents of the media on a USB thumb drive and mount the thumb drive as a drive letter. For example, mount the thumb drive as “D:”.
-
Run the following commands from a command window as an administrator. Type each of the following commands, and then press Enter.
COPY D:\EFI\MICROSOFT\BOOT\BCD D:\EFI\MICROSOFT\BOOT\BCD.BAK
bcdboot c:\windows /f UEFI /s D: /bootex
COPY D:\EFI\MICROSOFT\BOOT\BCD.BAK D:\EFI\MICROSOFT\BOOT\BCD
If a device has the Secure Boot settings reset to the defaults after applying the mitigations, the device will not boot. To resolve this issue, a repair application is included with the July 9, 2024 updates that can be used to reapply the “Windows UEFI CA 2023” certificate to the DB (mitigation #1).
NOTE Do not use this repair application on a device or system that is described in the Known Issues section.
-
Go to a device where the July 9, 2024 updates have been applied.
-
In a command window, copy the recovery app to the flash drive using the following commands (assuming the flash drive is the “D:” drive). Type each command separately and then press Enter:
md D:\EFI\BOOT
copy C:\windows\boot\efi\securebootrecovery.efi
D:\EFI\BOOT\bootx64.efi
-
On the device that has the Secure Boot settings reset to the defaults, insert the flash drive, restart the device and boot from the flash drive.
Timing of updates
Updates are released as follows:
-
Initial Deployment This phase started with updates released on May 9, 2023, and provided basic mitigations with manual steps to enable those mitigations.
-
Second Deployment This phase started with updates released on July 11, 2023, which added simplified steps to enable the mitigations for the issue.
-
Evaluation Phase This phase will start April 9, 2024, and will add additional boot manager mitigations.
-
Deployment Phase This is when we will encourage all customers to begin deploying the mitigations and updating media.
-
Enforcement Phase The Enforcement Phase that will make the mitigations permanent. The date for this phase will be announced at a later date.
Note The release schedule may be revised as needed.
This phase has been superseded by the Windows security updates release on or after April 9, 2024.
This phase has been superseded by the Windows security updates release on or after April 9, 2024.
With this phase, we are asking that you test these changes in your environment to make sure that the changes work correctly with representative sample devices and to get experience with the changes.
NOTE Instead of trying to exhaustively list and untrust vulnerable boot managers as we did in the previous deployment phases, we are adding the “Windows Production PCA 2011” signing certificate to the Secure Boot Disallow List (DBX) to untrust all boot managers signed by this certificate. This is a more reliable method for ensuring that all previous boot managers are untrusted.
Updates for Windows released on or after April 9, 2024, add the following:
-
Three new mitigation controls that replace the mitigations released in 2023. The new mitigations controls are:
-
A control to deploy the “Windows UEFI CA 2023” certificate to the Secure Boot DB to add trust for Windows boot managers signed by this certificate. Note that the “Windows UEFI CA 2023” certificate might have been installed by an earlier Windows update.
-
A control to deploy a boot manager signed by the “Windows UEFI CA 2023” certificate.
-
A control to add the “Windows Production PCA 2011” to the Secure Boot DBX which will block all Windows boot managers signed by this certificate.
-
-
The ability to enable mitigation deployment in stages independently to allow more control in deploying the mitigations in your environment based on your needs.
-
The mitigations are interlocked so that they cannot be deployed in the incorrect order.
-
Additional events to know the status of devices as they apply the mitigations. See KB5016061: Secure Boot DB and DBX variable update events for more details on the events.
This phase is when we encourage customers to begin deploying the mitigations and managing any media updates. The updates includes the following change:
-
Added support for Secure Version Number (SVN) and setting the updated SVN in the firmware.
The following is an outline of the steps to deploy in an Enterprise.
Note Additional guidance to come with later updates to this article.
-
Deploy the first mitigation to all devices in the Enterprise or a managed group of devices in the Enterprise. This includes:
-
Opting in to the first mitigation that adds the “Windows UEFI CA 2023” signing certificate to the device firmware.
-
Monitoring that devices have successfully added the “Windows UEFI CA 2023” signing certificate.
-
-
Deploy the second mitigation that applies the updated boot manager to the device.
-
Update any recovery or external bootable media used with these devices.
-
Deploy the third mitigation that enables the revocation of the “Windows Production CA 2011” certificate by adding it to the DBX in the firmware.
-
Deploy the fourth mitigation that updates the Secure Version Number (SVN) to the firmware.
The Enforcement Phase will be at least six months after the Deployment Phase. When updates are released for the Enforcement Phase, they will include the following:
-
The “Windows Production PCA 2011” certificate will automatically be revoked by being added to the Secure Boot UEFI Forbidden List (DBX) on capable devices. These updates will be programmatically enforced after installing updates for Windows to all affected systems with no option to be disabled.
Windows Event log errors related to CVE-2023-24932
The Windows Event log entries related to updating the DB and DBX are described in detail in KB5016061: Secure Boot DB and DBX variable update events.
The “success” events related to applying the mitigations are listed in the following table.
|
Mitigation Step |
Event ID |
Notes |
|
Applying the DB update |
1036 |
The PCA2023 certificate was added to the DB. |
|
Updating the boot manager |
1799 |
The PCA2023 signed boot manager was applied. |
|
Applying the DBX update |
1037 |
The DBX update that untrusts the PCA2011 signing certificate was applied. |
Frequently Asked Questions (FAQ)
-
See the Recovery Procedure section to recover the device.
-
Follow the guidance in the Troubleshooting Boot Issues section.
Update all Windows operating systems with updates released on or after July 9, 2024 before you apply the revocations. You might be unable to start any version of Windows that has not been updated to at least updates released on July 9, 2024 after you apply the revocations. Follow the guidance in the Troubleshooting Boot Issues section.
See the Troubleshooting boot issues section.
Troubleshooting boot issues
After all three mitigations have been applied, the device firmware will not boot using a boot manager signed by Windows Production PCA 2011. The boot failures reported by firmware are device specific. Please refer to the Recovery procedure section.
Recovery procedure
If something goes wrong while applying the mitigations and you are unable to start your device or you need to start from external media (such as a thumb drive or PXE boot), try the following suggestions:
-
Turn off Secure Boot. This procedure differs between device manufacturers and models. Enter your devices UEFI BIOS menu and navigate to the Secure Boot settings and turn it off. Check documentation from your device manufacturer for specifics on this process. More detail can be found in Disabling Secure Boot.
-
Reset Secure Boot keys to factory defaults.
If the device supports resetting the secure boot keys to factory defaults, perform this action now.
NOTE Some device manufacturers have both a “Clear” and a “Reset” option for Secure Boot variables, in which case “Reset” should be used. The goal is to put the Secure Boot variables back to the manufacturers default values.
Your device should start now but note that it is vulnerable to boot-kit malware. Make sure to complete Step 5 of this recovery process to re-enable Secure Boot.
-
Try to start Windows from the system disk.
-
Logon to Windows.
-
Run the following commands from an Administrator command prompt to restore the boot files in EFI system boot partition. Type each command separately and then press Enter:
Mountvol s: /s
del s:\*.* /f /s /q
bcdboot %systemroot% /s S:
-
Running BCDBoot returns “Boot files successfully created.” After this message is displayed, restart the device back to Windows.
-
-
If Step 3 does not successfully recover the device, reinstall Windows.
-
Start the device from existing recovery media.
-
Proceed to install Windows by using the recovery media.
-
Logon to Windows.
-
Restart Windows to verify that the device starts back to Windows.
-
-
Re-enable Secure Boot and restart the device. Enter the device UEFI menu and navigate to the Secure Boot settings and turn it on. Check documentation from your device manufacturer for specifics on this process. More information can be found in the "Re-enable Secure Boot" section.
References
-
Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign
-
For events that are generated when applying DBX updates, see KB5016061: Addressing vulnerable and revoked Boot Managers.
The third-party products that this article discusses are manufactured by companies that are independent of Microsoft. We make no warranty, implied or otherwise, about the performance or reliability of these products.
We provide third-party contact information to help you find technical support. This contact information may change without notice. We do not guarantee the accuracy of this third-party contact information.
|
Date of change |
Description of change |
|
July 9, 2024 |
|
|
April 9, 2024 |
|
|
December 16, 2023 |
|
|
May 15, 2023 |
|
|
May 11, 2023 |
|
|
May 10, 2023 |
|
|
May 9, 2023 |
|
|
June 27, 2023 |
|
|
July 11, 2023 |
|
|
August 25, 2023 |
|










